Using Nuclei At Mass Scale
Nuclei is an extremely powerful tool in Bug Bounty. Too bad most people use it the wrong way! Let me show you the top things that you should know to do better than the majority using this tool.
I’m pretty sure that most people who are getting duplicates are just using nuclei out of the box without any customizations. It’s the wrong way to approach the problem! You should not be thinking about being the first to find the bug, but think outside the box to find the bug. You won’t believe that there are so many people already doing automation without proper planning. Let me help you to improve bit by bit, step by step just showing some useful tuning for this tool to be more efficient.
Tip #1 – Tech Detect Before Running Aggressive Scans
The first thing I want to show you is actually what not to do – it’s running aggressive scans before detecting the technology. I’ve made this mistake so many times as well, so I want other people to avoid this mistake at all costs. To understand it better, let’s give a scenario:
For instance, you have found zero days on some kind of open-source project, either by yourself or with help from another person. You have made a custom nuclear template, to exploit that zero day. You ran across millions of targets that have you collected during your recon sessions and you have received zero hits…

What have you done wrong here? It’s actually a bad idea to send aggressive nuclei templates – for instance, ones that are using SQL injection, LFI, or any other aggressive payloads on a mass scale because of the web application firewalls again.
If you look at the diagram below, imagine you are controlling multiple servers and through those servers, you might be sending requests to different kinds of programs which might have different sets of servers:
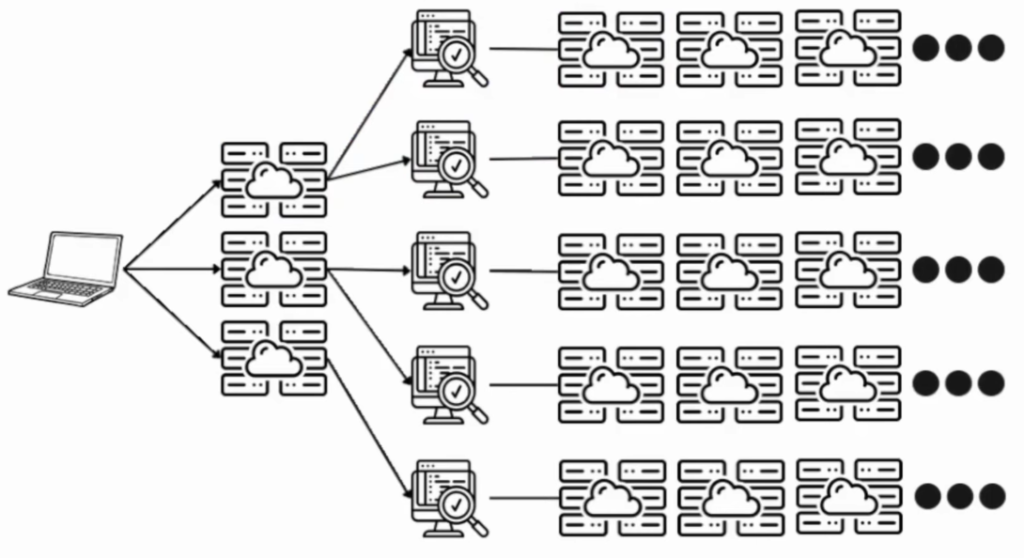
If you are sending aggressive nuclei templates, they will go through different servers, and at the beginning, they might not trigger any web application firewall:
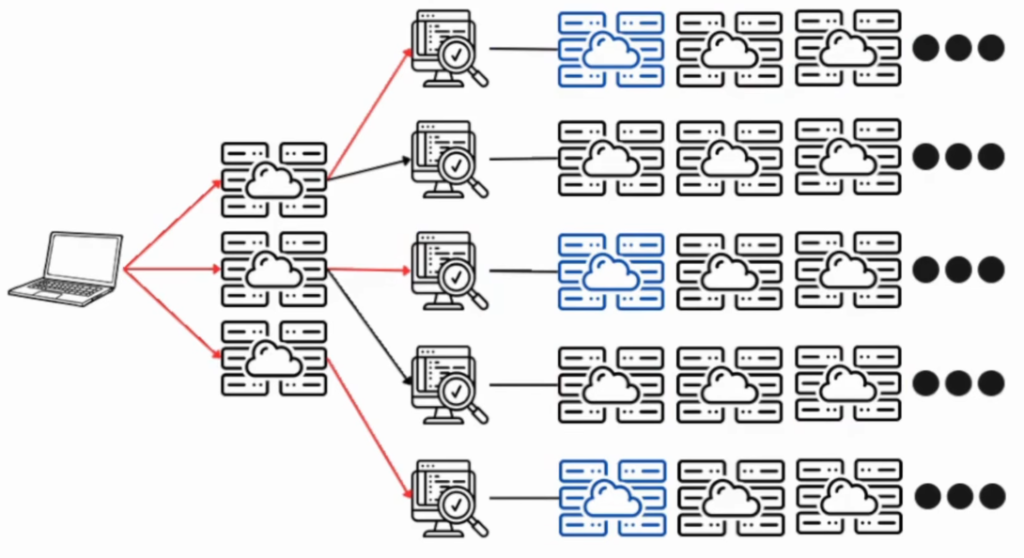
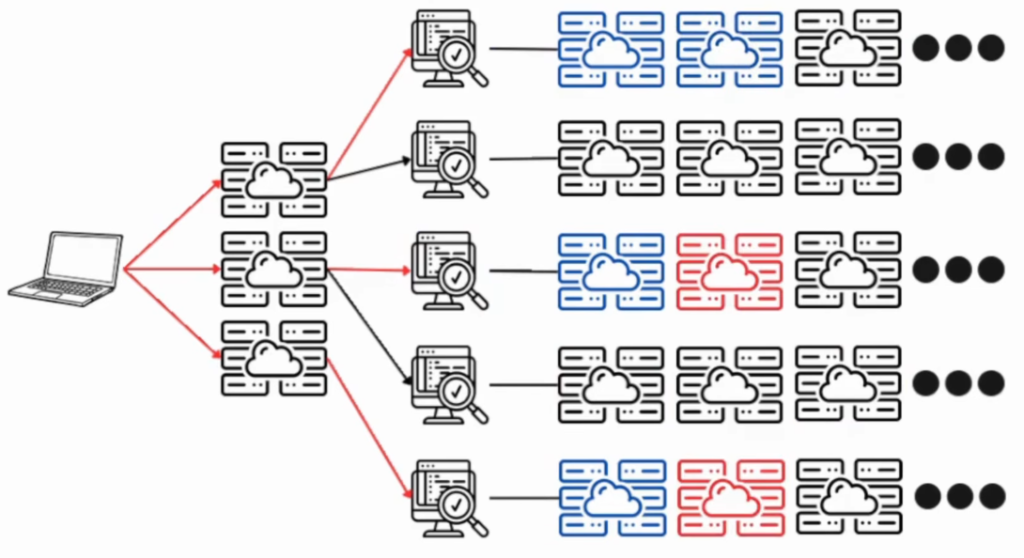
Requests will go through but eventually, for instance, on program 3 and program 5 (from the top to bottom) – the web application firewall would trigger after sending some requests:
Your controlled server 2 (from the top to bottom), won’t be able to send further requests for program 3 and program 4 and requests for server 3, on program 5 will be blocked as well:
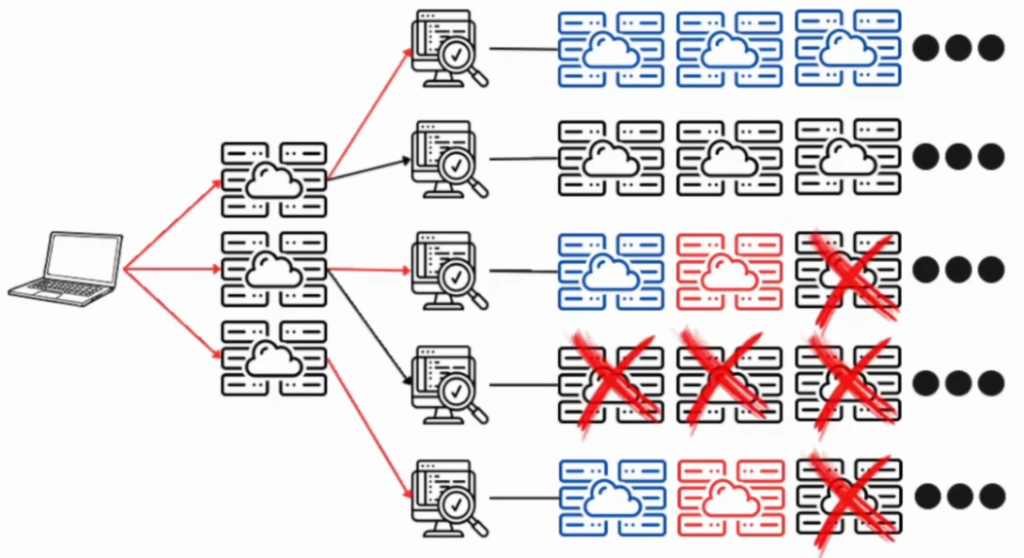
This is a pretty huge deal if you want to properly monetize your 0-day. You might miss millions or thousands of targets by running too aggressive payloads at first. A simple solution for this – is just to detect the technologies first, before doing anything crazy. The server list of your targeted technology will be much smaller. Scanning a couple of thousand or hundred websites instead of a million is the way to go.
To detect technologies, you either build another nuclei template, just for pinging the server, just checking for a specific endpoint without doing anything intrusive or maybe just using Google dorking as well, just to know that there is a vulnerable technology out there.
Tip #2 – Use Nuclei Flags to Bypass WAF
It’s pretty hard to not go fully undetectable and not trigger a web application firewall but there are a couple of tricks that you should include in your nuclei scans to limit WAF detections. Nuclei has a lot of configuration options:
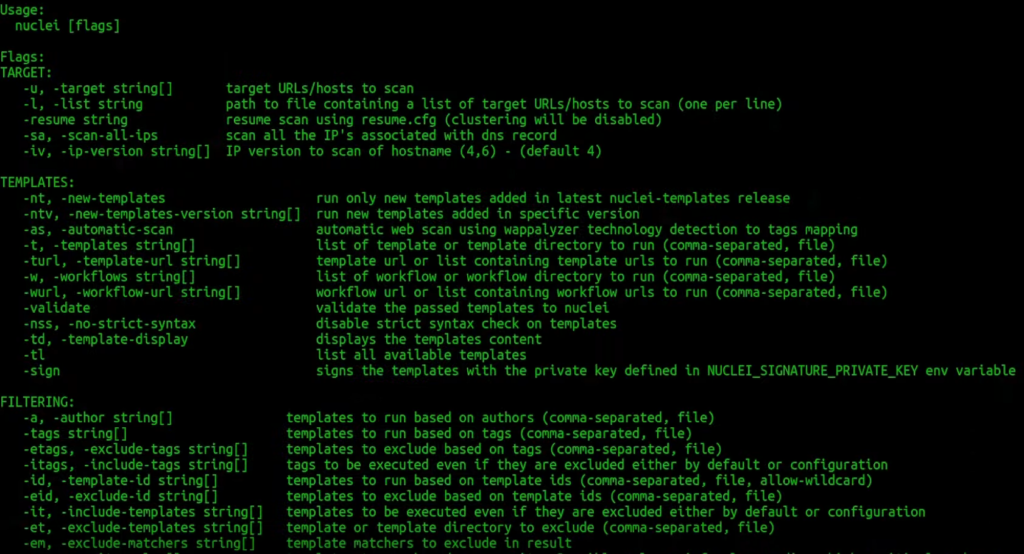
To avoid analysis paralysis, I will help you to focus only on those flags that are important, just to avoid web application firewall basic rules. If you go to the configurations, there is -H or header flag which basically helps you to set up your custom header:
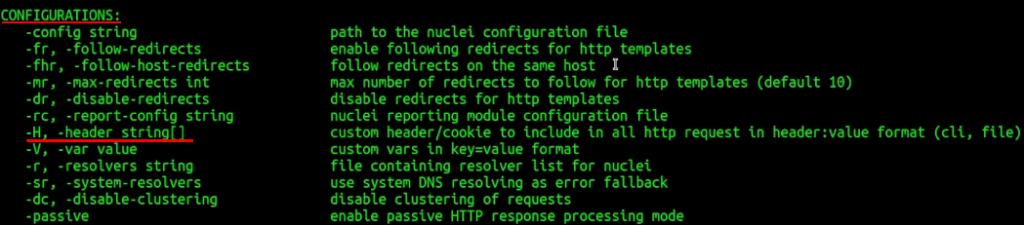
It usually helps to use certain custom headers like “User-agent” and just pass your regular browser user agent. A couple more good headers to use are the “Referer” and “X-Forwarded-For”. The final nuclei command would look similar to this:
cat targets.txt | nuclei -t your-template.yaml -H "User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:125.0) Gecko/20100101 Firefox/125.0" -H "Referer: 127.0.0.1" -H "X-Forwarded-For: 127.0.0.1" Of course, after all, you have to do your own research on custom headers, which actually helps to get most of the results.
Other important nuclei options or sets of options are right here – rate limit ones:
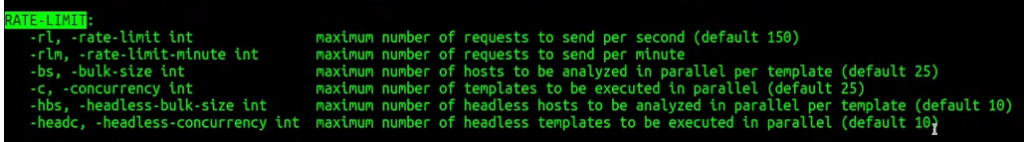
As you can see, by default, it’s pretty aggressive, and if you want to be more accurate, you should decrease those. Of course, it will affect the speed time to run but if you have a limited set of targets when you did your research, detected by technology and you are ready to run aggressive scans, you should play around with those headers.
Finally, the last nuclei option which is also very important is the scan strategy:
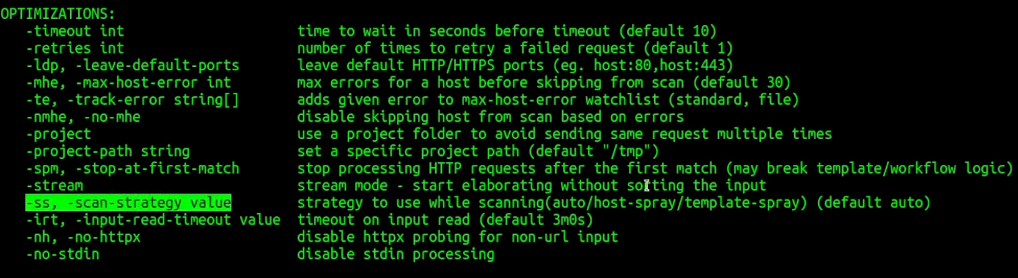
You should always set a host-spray strategy if you are running against millions or hundreds of thousands of results. It will look less aggressive for most of the web application firewalls.
Tip #3 – Do Not Run Nuclei Templates Blindly
Another important tip is not to run nuclei templates blindly. I’m talking about templates that you have borrowed either from another researcher or found on GitHub. Default nuclei templates are on the repository by project discovery but there are many others, pasted by other people. There could be a repository with 40k nuclei templates, so if you try the YOLO approach and blindly start running most of them, you will definitely get in trouble.
For example, there are some denial-of-service attack templates, and if you try running DOS on some programs, you could seriously get in trouble.
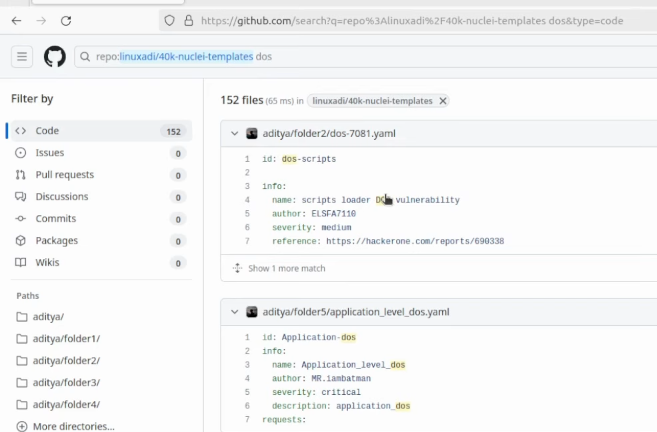
Always always read it and try to understand it before doing anything.
Bonus Tip – Building Wordlist Out of Existing Templates
The next tip I going to show you is a bit advanced – it’s not just using this tool but checking its templates for fuzzing and building a unique word list. Imagine you have ended up checking the WordPress site and you want just to build the wordlist to check like a basic vulnerable endpoint for WordPress. What you can do actually, is go to the default nuclei templates directory and try to collect endpoints from existing templates of WordPress. If you have installed nuclei, those templates should be in your home directory:
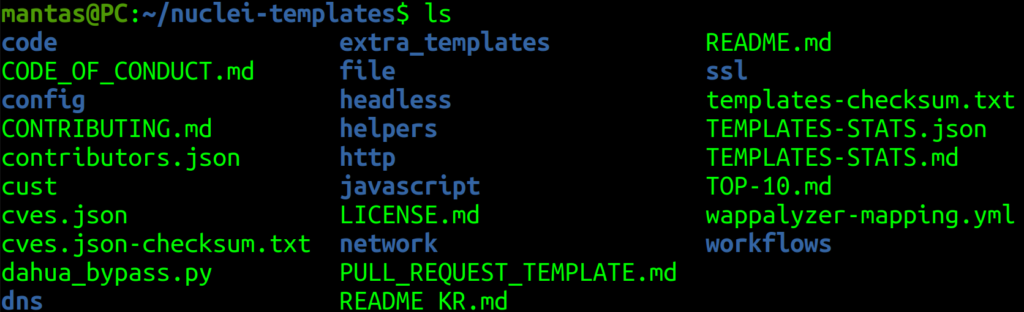
The http directory I think it’s most important if you’re hacking through the web and it also has many different sets of directories as well. If we check at least one of those, there are a couple of ways how a request could be sent – either by using http or raw http request methods. We will try to get all http request templates that will have {{BaseURL}}/endpoint. Also, we will filter out only endpoints that have a tag of wordpress. The recursive grep command will help us a lot:
cd ~/nuclei-templates/http && grep -R tags | grep wordpress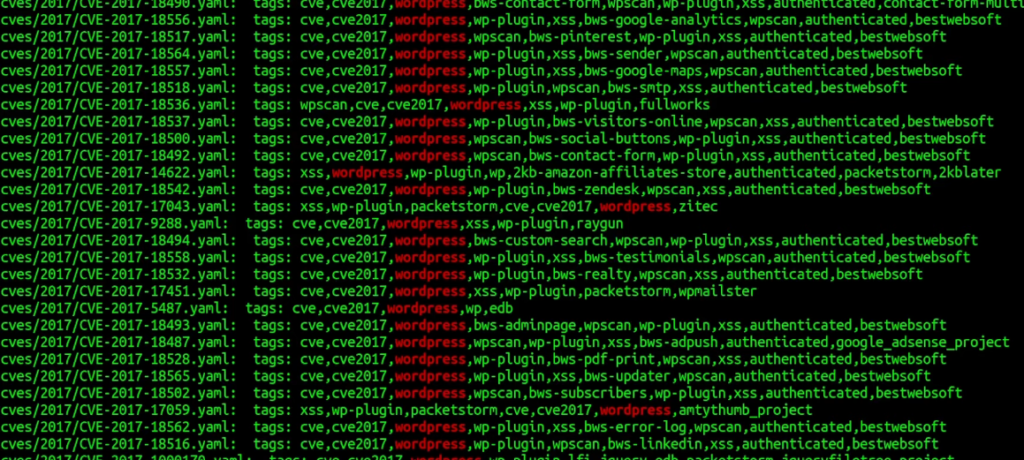
From those, you want only to get the filenames that have yaml file as well:
grep -R tags | grep wordpress | grep yaml | awk -F: '{print $1}'For each of those files, you can set it in the loop and try to cat it out:
for i in `grep -R tags | grep wordpress | grep yaml | awk -F: '{print $1}'`; do cat $i; doneIt will cat out all the templates but from all of those catted-out templates, you want to just select the lines that contain the “BaseURL” string:
for i in `grep -R tags | grep wordpress | grep yaml | awk -F: '{print $1}'`; do cat $i | grep "BaseURL}}/"; done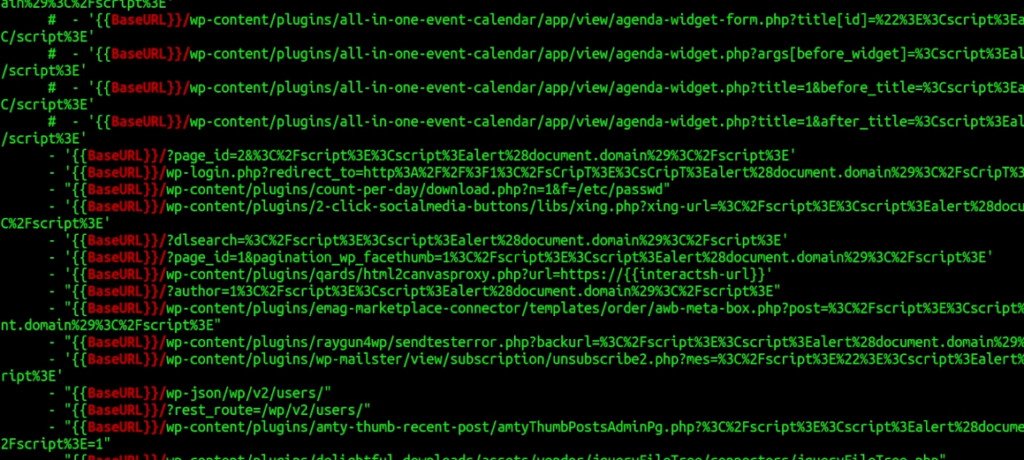
Lastly, what is left to do is only show the endpoints. We will use awk tool and “{{BaseURL}}” as a separator:
for i in `grep -R tags | grep wordpress | grep yaml | awk -F: '{print $1}'`; do cat $i | grep "BaseURL}}/" | awk -F '{{BaseURL}}' '{print $2}'; done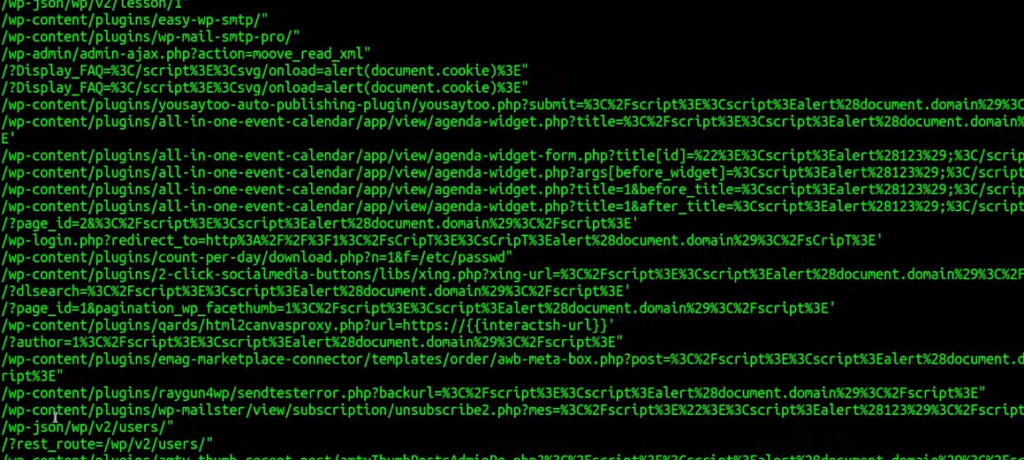
As you can see, you will get a lot of endpoints that could be used for building a custom wordlist. For sure, you want to filter out something and leave only the ones that might look interesting for fuzzing. I am just giving you an idea what you could do and the sky is the limit.
Last Thoughts
Hopefully, this article has improved your nuclei knowledge. This is just the tip of the iceberg as this tool is constantly being developed.
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!