Make Money 💸 Using Google Hacking
Imagine finding critical security issues just by using Google Search. Yes, it is possible! You’re about to enter into the world of Google Hacking – AKA Google Dorking. It’s a secret method of many bug bounty hunters to get to the top of the scoreboard. Many think of Google as a just search engine but in reality, it could be a more powerful tool for hacking. For instance, a lot of cyber criminals just use Google alone to compromise many websites. They have been using Google Dorking techniques and tricks to do bad stuff. Of course, we are good people and we want to provide value for the companies to improve their security. Google will be our best friend in this case. Forget about simple keyword searches! We are about to deep dive into the world of advanced search techniques.
The “site:target.com” Dork
Usually when I am approaching the target, I check for wildcard domains using the site keyword. Use it with your target domain, for example – site:target.com. I will show you the results only from target.com and its subdomains.
Let’s use the Coca-Cola program as an example. They have a lot of wildcards to check on since almost every brand and website owned is in scope. So, if I want to go after its main domain, I will use site:coca-cola.com dork:
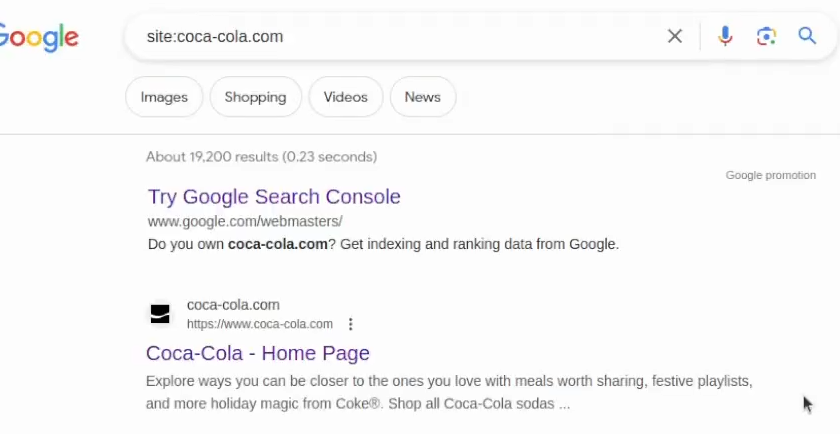
As you can see, there are more than 19k results. I could try getting less results if I try other Top-Level Domains, like us – for example site:coca-cola.us. If I want to get all TLDs results, I can use the site:coca-cola.* dork:
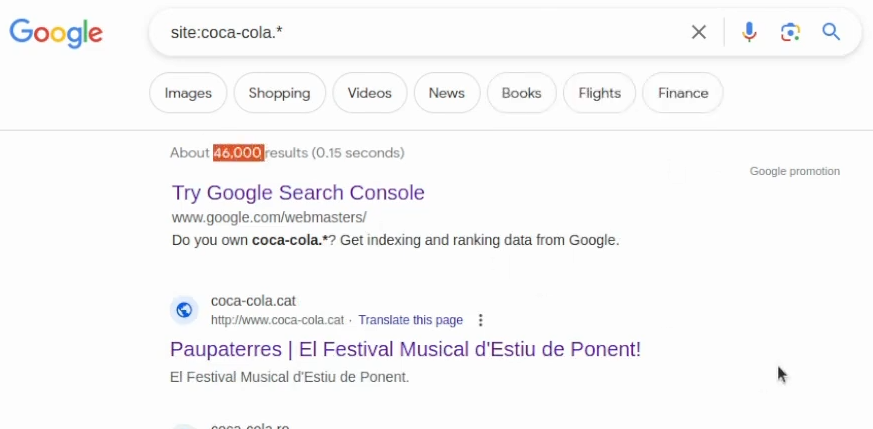
Note: when I do Google Dorking, the site keyword usually goes first in my query.
The “ext:<file extension>” Dork
Next what I want to check for is – extensions. For this case, I use the ext keyword. Either it could be pdf files, it could be xlsx or xls. It’s just a matter of your imagination on what you could try experimenting on. For this example, if I want to get PDF files, I could try using ext:pdf dork. I would also want to filter them out using extra keywords. What goes along well with pdf type of files is classified or confidential keywords. So, the final query will look like this:
site:coca-cola.* ext:pdf classifiedOR
site:coca-cola.* ext:pdf confidentialThose are pretty much low-hanging fruits, but of course, you want to take a look inside these files for sensitive data to be extra sure before reporting! You should always check for pdf files and xls and xlsx, even doc and docx or PowerPoint files could be awesome to check for sensitive data.
The next interesting thing that you could look for is server-side file extensions. You want to check for php, jsp, asp, aspx, sometimes even .action extensions, for example:
site:coca-cola.* ext:phpAdditionally, the last extension worth looking at could be zip files, backup files or log files.
The “intitle:<keyword>” Dork
Another filtering keyword that could be used is intitle. It will search through the titles of websites. You could use double quotes if you include two words as a keyword with this. For example, to check sites with an “index of”, you could use the following dork:
site:target.* intitle:"index of"This might work on targets that are pretty huge or not well-tested.
The “inurl:<keyword>” Dork
The last dork that usually use in my dorking sessions is inurl. It will filter through Google results by checking keywords in their URL. This could be used along with ext: with common server-side extensions. For instance, I could check for php file extensions along with common parameters that have a higher chance of having SQLi:
site:target.* ext:php inurl:idor
site:target.* ext:php inurl:catDiscovering Root Domains
The next thing that this Google Dorking could be used for – is discovering other top-level domains. For example, if we go to the main site coca-cola.com, and we check for the footer, we will see “© 2024 The Coca‑Cola Company. All rights reserved.” at the bottom. Let’s copy this one even with a copyright symbol and paste it into the Google search bar:

Using this method, you might find some extra root domains. You might want to check if it truly belongs to that company as well. Another thing you should do is remove some words from your query, for this example – remove 2024 year:
"The Coca‑Cola Company. All rights reserved."I’ve found an extra domain – cokeconsolidated.com, just because I had removed the 2024:
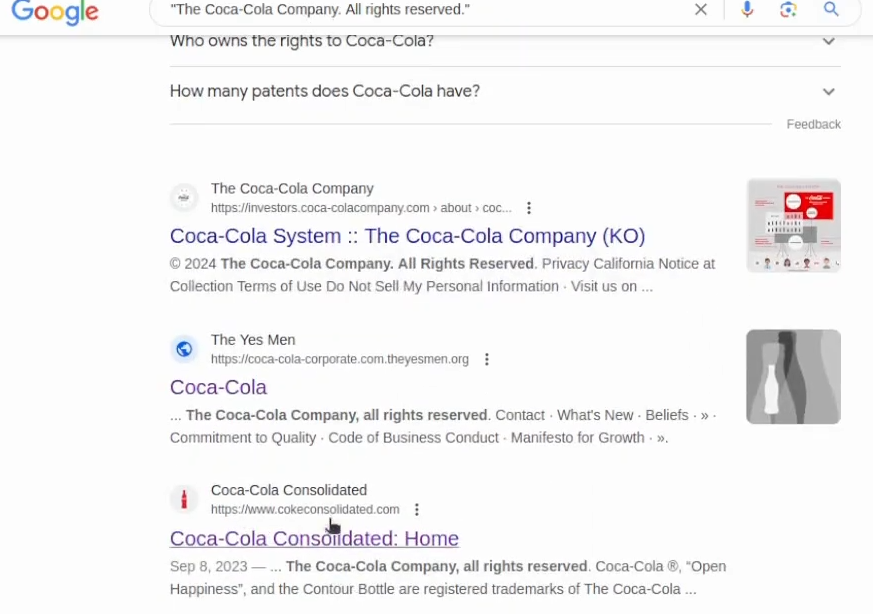
One more thing I suggest is to check the main website and inspect brands. This might get you some leads on what other root domains to use with site dork. For example, I have found that sprite.com and fanta.com would also be potential candidates for search queries. Make sure to also inspect their footers to get even more leads! Do this a lot until you get like large scope of top-tier domains. From that point on you can do subdomain enumeration.
Filtering Out Search Results
Other things that you also want to include in your Google Dorking are keywords to limit your search results. For example, if I want very old sites you can use a minus symbol and append it to your existing query with keywords like this:
"The Coca‑Cola Company. All rights reserved." -2024 -2023 -2022 -2021The minus symbol plus keyword will filter out the pages that have pretty recent years in their footers. This example is pretty specific for this target, but you should always play around with your program, try to understand how they construct pages, and form your Google queries according to it.
Another thing that you also might want to check is register endpoints. It has a register, you can use inurl:register for this or try without it as well:
"The Coca‑Cola Company. All rights reserved." inurl:registerOR
"The Coca‑Cola Company. All rights reserved." registerAdditionally, you should exclude www sites since those usually are tested by the majority of hunters:
"The Coca‑Cola Company. All rights reserved." register -wwwAlso, you might want to check for other strings to find register endpoints like “sign up”, “sign in”, login, etc.
Getting Ideas For Fuzzing
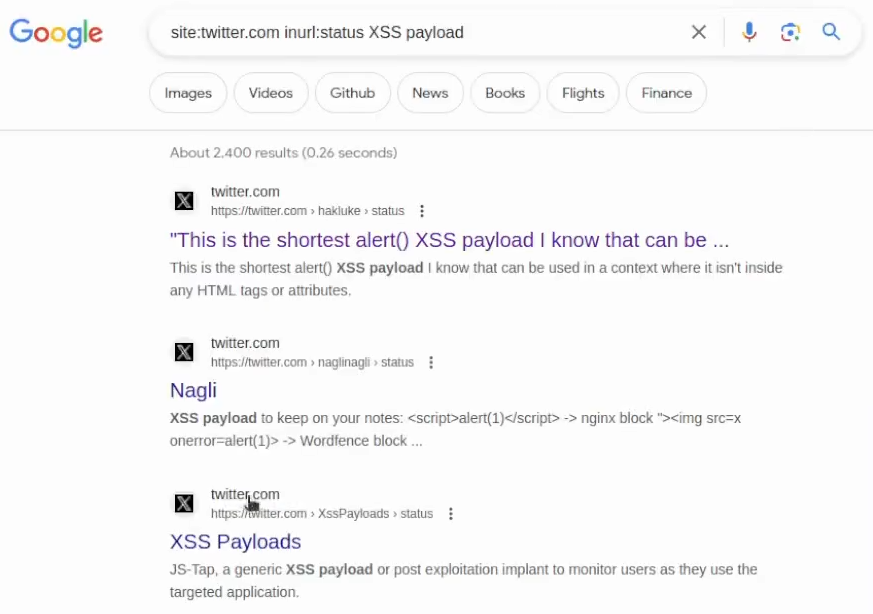
Even if you are not doing bug bounty hunting at the moment – Google Dorking could be used for getting ideas for your pentest or just testing. For example, you can use Twitter search but for me, I found more value in just using Google to get ideas from Twitter. So I use site:twitter.com with inurl:status. So if I want to get some ideas for XSS payloads, I will use the following search:
site:twitter.com inurl:status XSS payloadAs you can see, Google will give me a good idea for the shortest alert() XSS payload along with other interesting ideas:
Also, alternatively, you might want to check famous blogs like medium.com which is pretty popular within the Bounty space:
site:medium.com XSS payloadYou can get some ideas from there, maybe infosecwriteups.com is also a good area to check for:
site:infosecwriteups.com XSS payloadMany people choose the HackerOne feed to research vulnerabilities, so you can utilize Google for this as well:
site:hackerone.com inurl:reports XSSGoogle is your very good friend you can use its search even if other sites have their own search. Another favorite place of mine good for checking CVE’s is Github:
site:github.com "CVE-2024"Google Dorking Resources
You can get inspiration on what you can do with Google Dorking using an exploit database, especially a Google hacking database. There are a lot of filters. Sometimes you can find filters by error messages and those error messages could lead to sensitive information being leaked or maybe just checking for vulnerable servers:
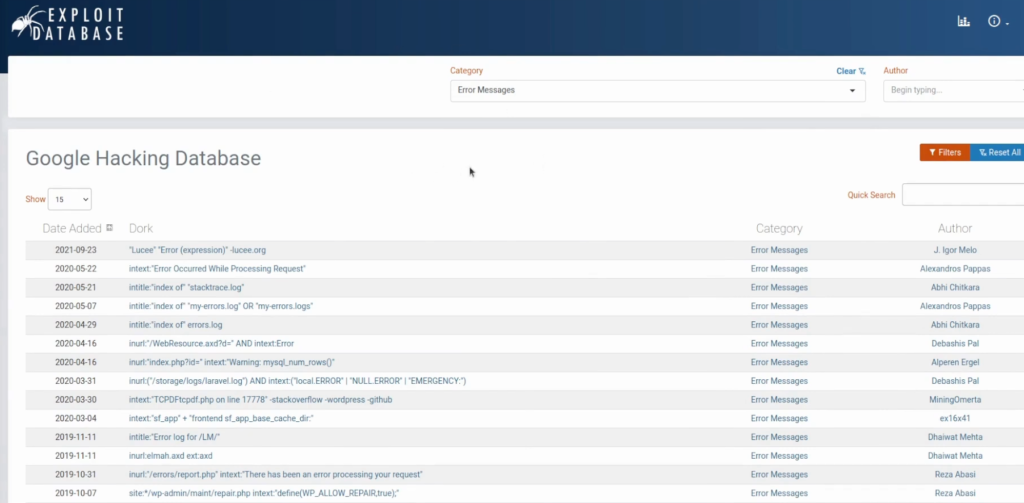
Alternatively, there is a GitHub page for Google dorking which I really like. I highly recommend using this one since it’s updated every day:

Get the ideas to check backups, logs, configuration files, grafana, kibana, or any other technology. You can do a lot of stuff, even for XSS only.

Last Thoughts
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!