Recon on Steroids – Discover EVEN MORE Subdomains
Won’t you love to find the website or asset that nobody else has found, test it, and find some serious vulnerability that will result in a big fat paycheck? Yes, it is possible! If you’re thinking outside the box! The big programs, which have “all our assets in scope”, “everything that they own in scope” or something similar mentioned in their policy, could unlock the path to finding untested areas. I will show my own unique methods to discover more core subdomains. This will probably even surprise the program managers when they realize that you have found an asset they have no idea that they own.
Main Website Recon
If you saw some of my videos from the recon playlist, you know that I show most of my examples of the Coca-Cola company. I usually prepare a list of root domains in the wildcards.txt file. Let’s try populating this file.
The first thing that I gonna show you, is just doing simply stupid recon – just going to the main website called coca-cola.com. In their vulnerability disclosure policy, they mentioned that all the brands of this company are basically in the scope. In this case, the first thing you should always do before even doing something intensive – is to go to the main website and try to write down as many brands as possible that they own. For example, sprite.com, fanta.com, and many others might be included since these brands do belong to them:

Of course, you have to verify those domains by just simply googling them. Just place terms like “Sprite” or “Fanta” in the search bar, and even more core domains with different TLDs will start appearing.
Certificate Recon
The next way to get core subdomains is by checking the certificate websites. I like to use crt.sh, passing the company organization name there. To get the company name, you can use Wikipedia, Crunchbase, or the simplest way – just by going to the footer and copying the company name:
Let’s use “The Coca-Cola Company” to paste it to the crt.sh:
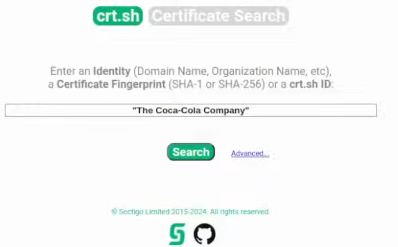
You always want to validate those domains because sometimes there will be cases when the domain was working 10 years ago and it was part of the company, but after a while, it stopped working, it could have been purchased by another company or just the domain was not used, stopped working or other person created the similar website or similar brand and used that domain name. So always validate the collected subdomains!
Additionally, what you can do is add &output=json to the end of the URL query and copy it to the terminal for further filtering. Use the curl command with jq to do some magic:
curl -s 'https://crt.sh/?q=%22The+Coca-Cola+Company%22&output=json' | jq '.[] | .common_name' -r | sort -uThe jq tool will filter out common names of certificates in the crt.sh website. The -r flag will show only the raw output and sort -u will leave unique results. There will be a lot of results but you will only need the core top-level domains. I suggest filtering them out using manual inspection and of course, validating them by going to the site directly or quickly running subfinder to check their subdomains.
Google Recon
Another way is just searching on Google by the footer. This time I suggest using an almost full footer string like “© The Coca-Cola Company. All rights reserved.” and paste it on the search bar:
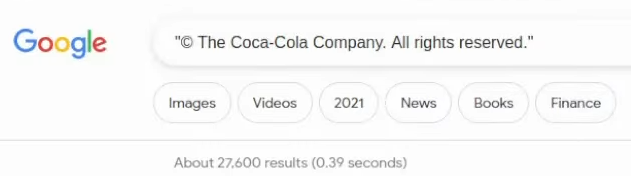
If you noticed, I have removed the year. It is a good idea to do this since it will also include some results of older websites that were updated a long time ago.
Shodan Search Engine
One more way is just using Shodan. Try to specify the company name using this dork:
org:"The Coca-Cola Company"You might want to replace it with your target company name and look for the hostnames. The Shodan usually includes them along with IP information. It’s another good area to collect root domains but as always, you have to double-check them first.
Fofa Search Engine
So the last one is one of my favorites – using fofa search engine, using favicons. Firstly, let’s try to search by the company name here in the quotes:

Next, you want to click on more and select the favicons that resemble the main logo of the company. In this case, it will be either a bottle or it could be Coca-Cola’s name.

Once again, like on Shodan, you will get a bunch of results that might have many hostnames to add to your list. Another tip is to use those favicon hashes that appear in the Fofa search bar for Shodan search. I have already mentioned this in my previous article about Shodan Dorking, so make sure to check that out!
Last Things
There might be even more ways to get some wildcard domains but those there are my favorites that I personally use. You have to use your imagination, think outside the box, and research current recon tools to get ahead in this Bug Bounty Game.
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
