Jump Over Firewall Finding Origin IP
Web application firewalls are the most annoying when you know that there is vulnerability out there! Usually, it’s old, not really well-maintained websites, so in most cases, it’s just easier to put WAF on top of them. What if I told you that there is a way to bypass this layer of protection – I’m talking about finding origin IP address as a method. We will explore multiple ways how you can do it.
Firewall Basics
This is a basic diagram of how a firewall works:
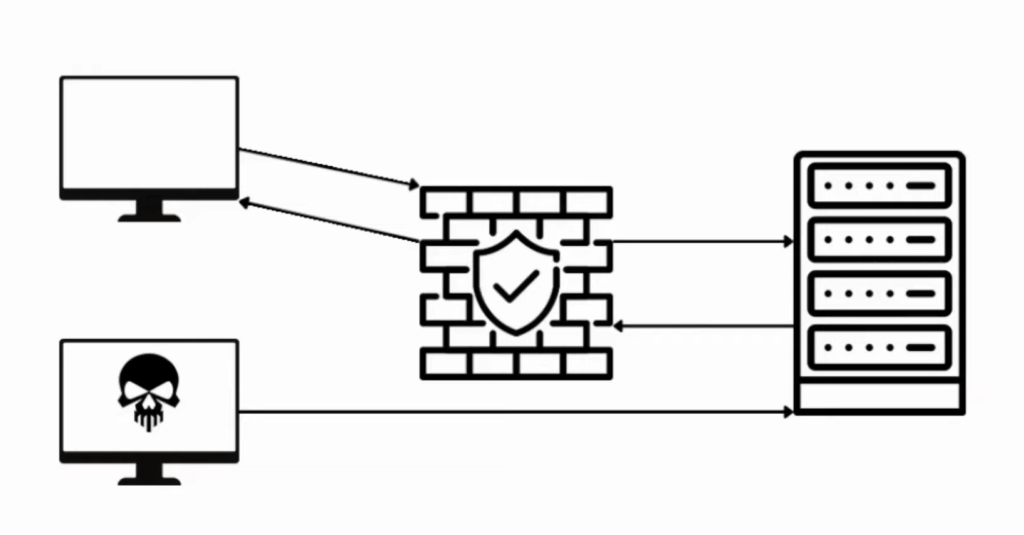
The regular user sends requests through the firewall, firewall checks the request if it’s legit, and passes that request to the server. Then the server processes that request, sends it back to the firewall and the firewall sends it to the client. It’s doing that because the origin server doesn’t want to disclose its own IP to the clients. On the other hand, a hacker (marked with a skull icon) doesn’t want to go through the middleman and wants to go to the server directly. If for example, you are sending SQL injection, XSS, or other payloads – those requests could be blocked by firewall rules. That’s why it’s a good idea to skip the struggle of bypassing WAF by knowing the location of the server – finding origin IP.
Sometimes there could be cases when the request could be blocked by the server itself, or sometimes there could be rerouting if for example going directly, it could be rerouted to the firewall as well but those cases are exceptions. This time we will try to find a way just by accessing the origin IP here and trying to communicate directly.
WAF Recon
The first thing that you should do always, is check if target truly has a web application firewall in place. There are a couple of easy ways to do that, so the first thing I like to do, is ping the target. In this example, I will ping my own website:
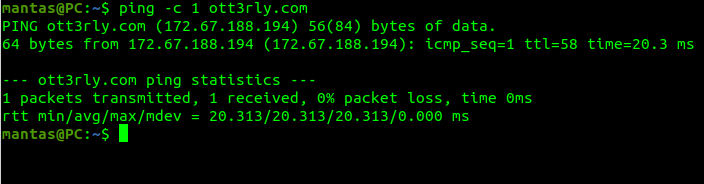
As you can see, it responds with IP. If it responds with that IP, it doesn’t mean that it will be like the origin IP of the server. It could be just a web application firewall IP address. If we try accessing it directly, it will show a regular Cloudflare error:

Another thing that you can do, is also use the Wappalyzer plugin. If you try to inspect this website, it will show that I’m using Cloudflare:

Another thing is also going back to the terminal and using tools like dnsrecon:
dnsrecon -d ott3rly.comThis command will access DNS records, which could also indicate what WAF the server could use:
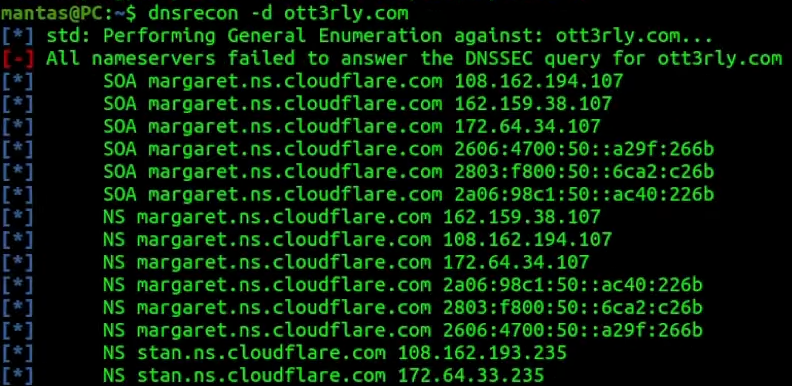
Sometimes you can leak the origin IP address if the server does not use any WAF but in this case, we can see a lot of Cloudflare name servers.
If you are not a big fan of CLI tools, alternatively you could also check who.is website.
Method #1 – Shodan
The next thing I recommend for finding origin IP is using Shodan. It’s also easy to check for a lot of leaked IPs by using a basic search. You can filter out those IPs to not include known WAF headers, responses, etc. I usually filter by 200 status code as well. I like to use SSL shodan dorks with those mentioned filters:

If you are interested in shodan dorking techniques, I have an article for that so make sure to check it out!
Method #2 – Censys
Another good tool for IP recon is using censys. Just paste your target in the search bar and you will be awarded with pretty interesting results:

As you can see, there are a lot of filtering options on the left side, so you can try some filtering as well. For example, Akamai, Amazon, and similar stuff are not interesting to us, so you should try filtering those out.
Method #3 – Security Trails
Lastly, my favorite method is using Security Trails. I recommend creating a free account and you could use it freely. This tool is good for targeting just a single website to get to know its IP address. I will use my own website as an example and try to access historical data:
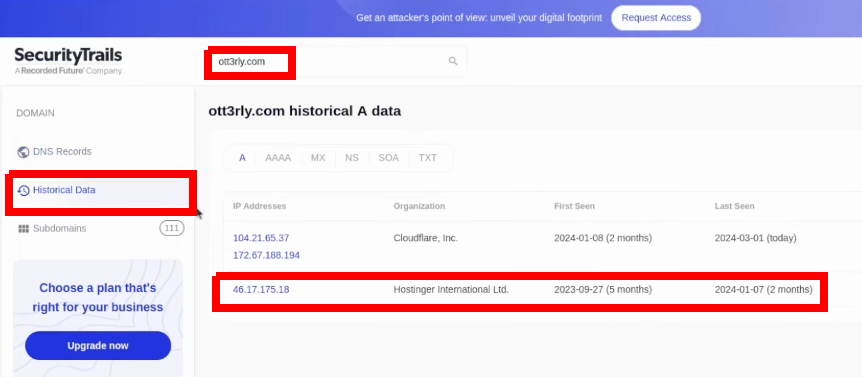
When I write ott3rly.com in the search bar and try to access Historial Data, the A DNS records are really worth looking. As you can see, before using Cloudflare, the website was not under WAF so its origin IP was leaked. In this case, it’s the hosting provider’s origin IP so it’s not a really big deal, but usually, in regular testing scenarios, you could stumble across the VPS IP address. In that case, there is a possibility to access the page directly by its IP.
Final Tips
If you try all of those methods on your target, you will have a chance to not be detected under WAF radar. It will make your life much easier when you need to do certain exploitation, like fuzzing XSS, SQL injections… So before even building a sophisticated payload, I highly encourage you to find the origin IP.
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
