Common 403 Bypasses Part 1
Are you tired of seeing those 403 Forbidden errors that block you while testing? Don’t worry, some effective techniques could help to avoid this hassle! Let’s explore some 403 Bypasses that work!
What is the 403 Status Code?
This status code limits users’ access to specific hosts, endpoints, etc. It could be implemented either in the web application code, or there could be certain Web Application Firewall rules. There might be different cases for bypasses because of different sets of technologies. So it does mean that there won’t be an all-in-one solution for most cases, but we will still explore the most common ways!
There are multiple techniques that we will try to cover in this writeup:
- Applying special characters to the URL
- Switching HTTP Methods
- Headers manipulation
- Switching IP or using a VPN provider
Fuzzing HTTP Methods
Let’s start with the method which is pretty easy to check. If you get 403 status just by trying to access a certain endpoint, while on other endpoints you are getting 200, this could be one of the first things to try. The idea is to check the web application’s handling of different HTTP methods (like GET, POST, PUT, DELETE, etc.), to see if changing them can lead to other status codes like 200. It is just as simple as that, to quickly check this, you could use an HTTP proxy like burp:
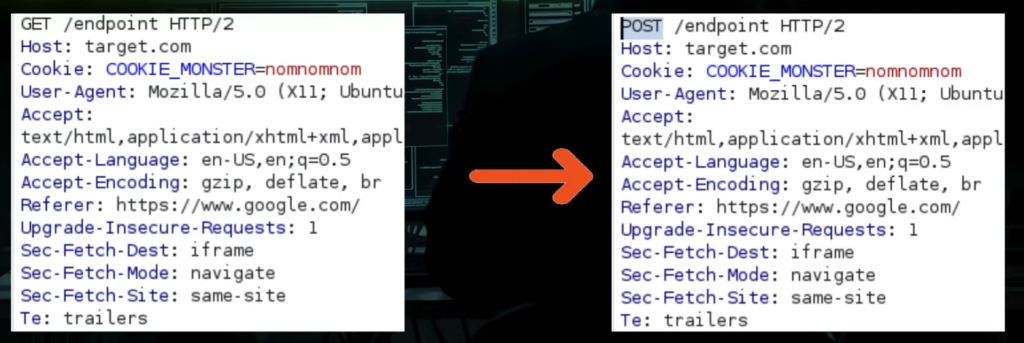
or you could send the request with CLI tools like curl:
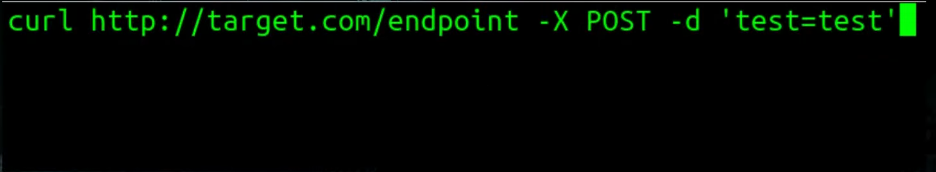
Headers Manipulation
Another technique could be used when you get a 403 code when trying to access a website for the first time. I do recommend trying to play around with those headers:
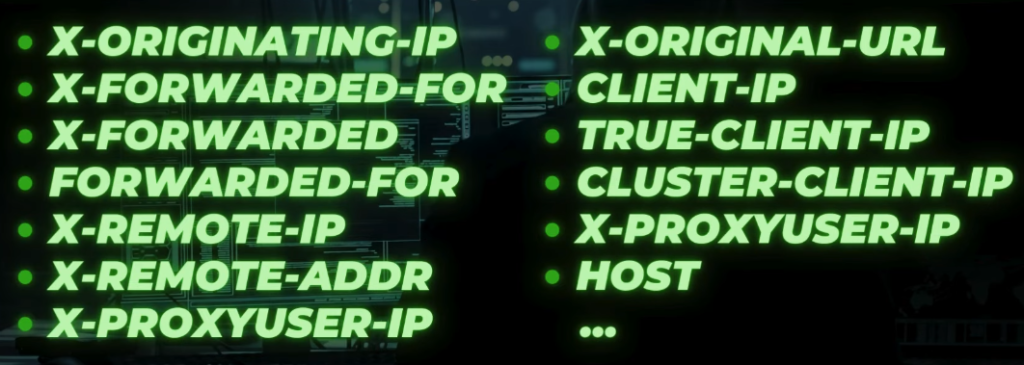
Together with them, you could use 127.0.0.1, localhost or even some cloud internal IPs could work as well:
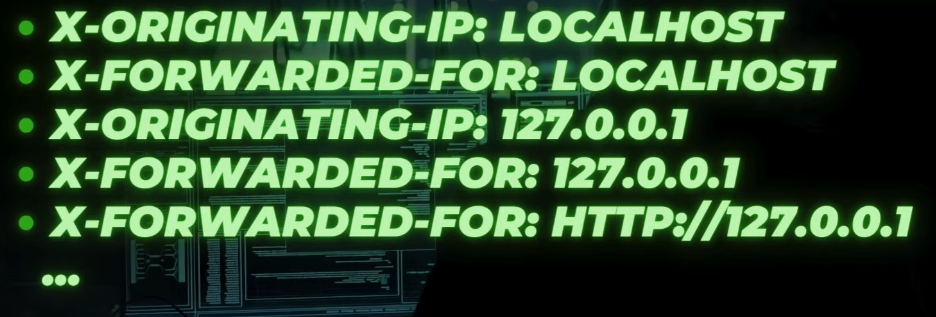
Some Burp Suite plugins do that, or you could inject just another header like this inside the request. I also use this with CLI tools as an extra header, for example, when using httpx at the mass scale:
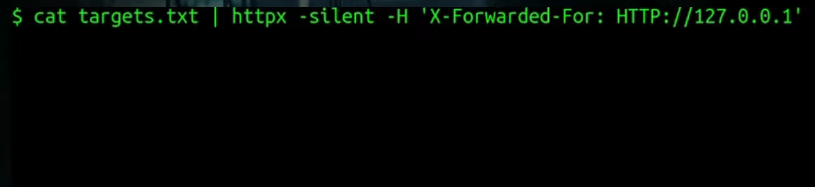
Changing IP Address or Using a VPN
You could also get blocked by a Web Application Firewall by doing malicious actions. For example, if you send too many requests containing known malicious payloads, using too many requests per second, trying to access known sensitive files, your IP might get blacklisted. Your IP could get blacklisted for a certain amount of time, or even indefinitely! For this reason, I do recommend having either an IP proxy, which could take more effort, or just using a VPN provider. I do use NordVPN, not for those reasons to access certain content, but mainly when I get blocked while testing! I do save a lot of time and nerves when using this product since others could be slow or not really reliable.
Fuzzing the URL Path
And the last one – is using some tricks to the URL path. I have had the most success with this one. Either if you having issues accessing the website for the first time, or a certain endpoint is not reachable, it is worth trying to send these payloads:
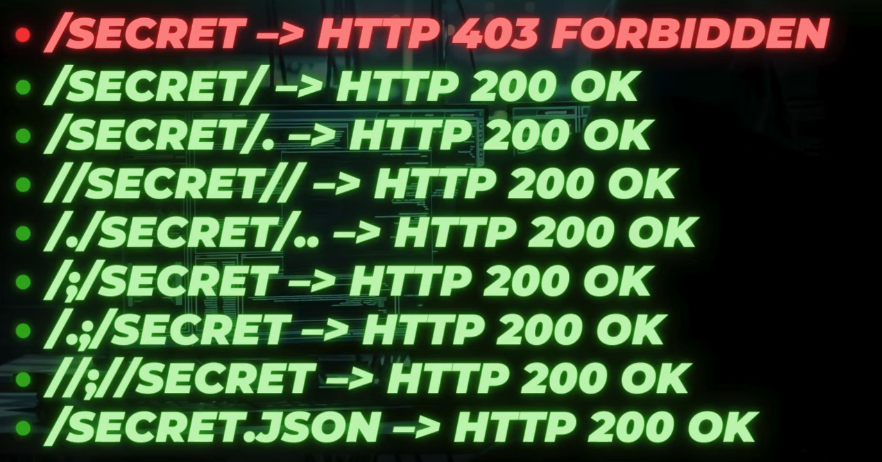
I have discovered some swagger documentation sites using this method, which eventually led me to discover a more severe bug – SQL injection.
Summary
As the introduction of 403 bypasses, we’ve covered some ways to tackle 403 Forbidden errors, from simple URL changes to sophisticated header manipulations. In the second part, we will dive into more techniques and I will also show you some of my favorite command line utilities to automate detection! It was my pleasure sharing this knowledge, wish you a nice hunt!
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
