Taking Bug Bounty to the Next Level: Mass Google Dorking Techniques
Many things have changed over the years, and the Google search engine is not the same anymore. It does not show many query results as previously, and it’s becoming harder and harder to use many working google search techniques. Having that in mind, there are still some good bounties being made everyday by the help of famous search engine. It is possible to find some pretty severe information disclosure vulnerabilities or get some leads about some juicy endpoints. On this article, I will cover some unusual ways that could help you find some high or critical severity vulnerabilities that not many people know about. I will show how it is possible to utilize some mass google dorking with the help of Google products themselves.

Technique #1: Firefox Plugins to Build URL Wordlist
As previously discussed in the Mass Cross Site Scripting article, I prefer to collect URL endpoints before testing for XSS and other vulnerabilities. I outlined two methods for accomplishing this: host crawling and utilizing web archive data. However, I have not mentioned that it is possible to employ Google search engine to build that list. I have selected a Firefox as my to go browser, since it has some unique plugins for this:
- Google Auto Load — allows automatically load next google page without need to click “More Results” button. As far as we know, instead of clicking page number, the Google Search engine have changed it to load more results. This plugin saves me some time, so I won’t need to bother clicking buttons at the end of the results page.

- FoxScroller — plugin which goes hand in hand with previous one. It basically allows the browser to automatically scroll to the end of the page by the click of the button.
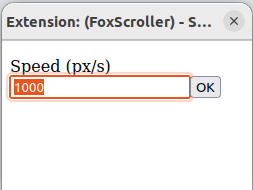
By default, it is pretty slow to scroll, but you can modify its speed easily:
- Link Gopher — extracts the URLs from the current page. This is the last part of this URL wordlist building puzzle. I use it when my scroll ends to the last google results page.
Now we can combine all 3 Firefox plugins to gather URLs of single target:

Technique 2#: Google Sheets Extension to Collect Google Search Results
To my knowledge, I haven’t seen anyone in the bug bounty community using this. Because of that, it could be a new approach to collect huge list of Google search results. Compared from the previous technique, this could be used with multiple targets at once. It’s a pretty efficient way to perform mass google dorking. Let’s open Google Sheets and explore this technique!
Google Workspace Marketplace has ImportFromWeb plugin available for Google Sheets application.
It basically allows using IMPORTFROMWEB() and IMPORTFROMGOOGLE() functions on sheets. If you have a dedicated list of Google dorks prepared, it could be used to gather results. For the demonstration of this extension, I have created a Google Sheet:

The first tab, called Targets, contains programs and their wildcard domains. I use this tab data for building dorks. To my experience, domains with few thousand google search results works best for this approach.

Dorks tab could be used to build some queries for the search engine from the existing target wildcards domains. As you can see, I use CONCATENATE() sheets function for each of domain from Targets tab. You could build different dorks, but make sure that they should have different results for each line here.

Finally, on the last tab called Search Results, I have used IMPORTFROMGOOGLE() function to get 100 results for each dork. For it to fully work, you need to specify dork as first argument, the second argument is the values you want, and the 3rd argument is query options, which is in this case is numResults (100 is maximum).
To view this process in action, I have created an example google sheet, to help understand fully how it works. Also, there is a video which explains in detail how IMPORTFROMGOOGLE() function works.
Technique 3#: Using Google’s Custom Search Engine
The last technique were inspired by famous Bug Hunter @HusseiN98D, so all kudos goes to him on this one. He made a tweet about using a custom search engine for all bug bounty programs. It made me realize that this could be a very powerful approach for findings some sensitive data. To my surprise, Google made a tool for you to customize your search, even embed to your own website if you want. It is the top gun for you mass google dorking! You can access this tool here: programmablesearchengine.google.com.
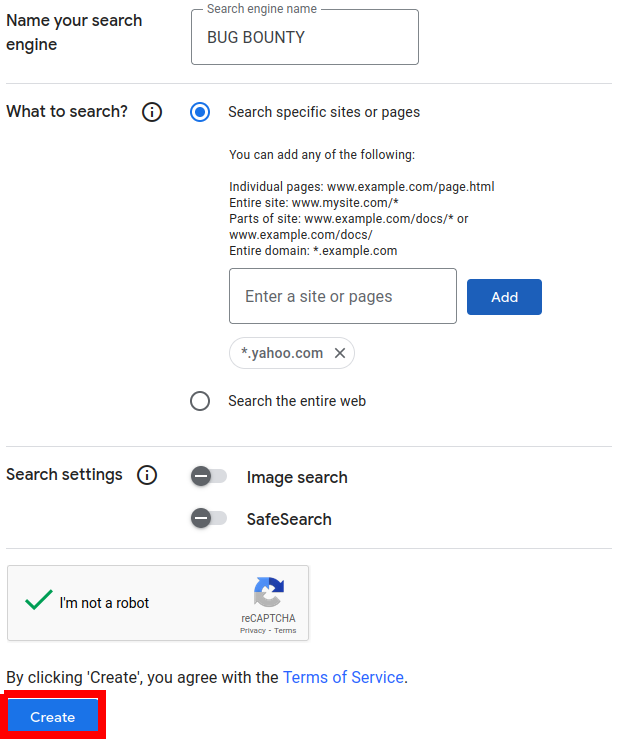
Once you clicked on Add button, give your own search engine the name, and you will be able to add your own website filtering:

For now, just add one wildcard, for example — *.yahoo.com and click create:
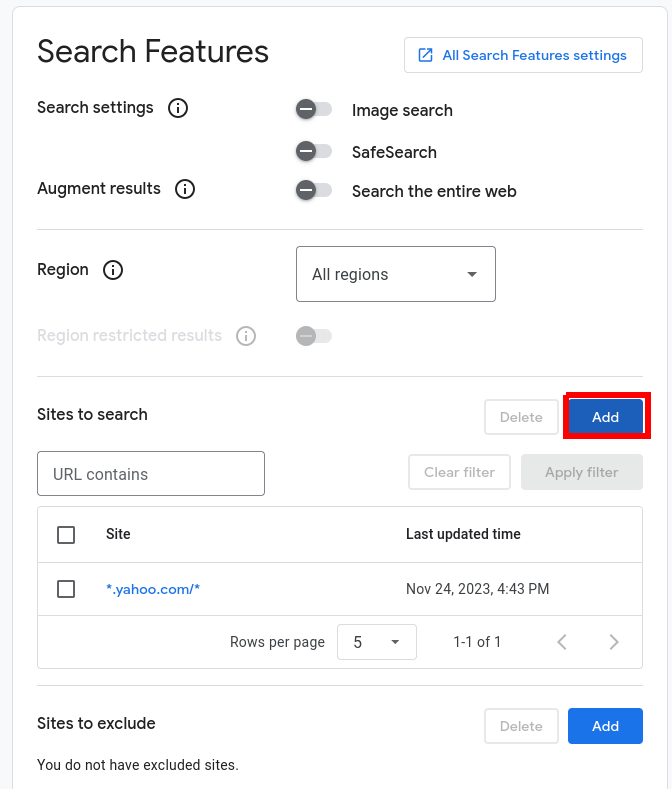
Next, when you click Customize and scroll to the Search Features, you can see that you could add wildcards even after a custom search engine was created. I suggest adding wildcards now (on edit mode), and not on the initial creation, since on edit mode you can add multiple websites at once:
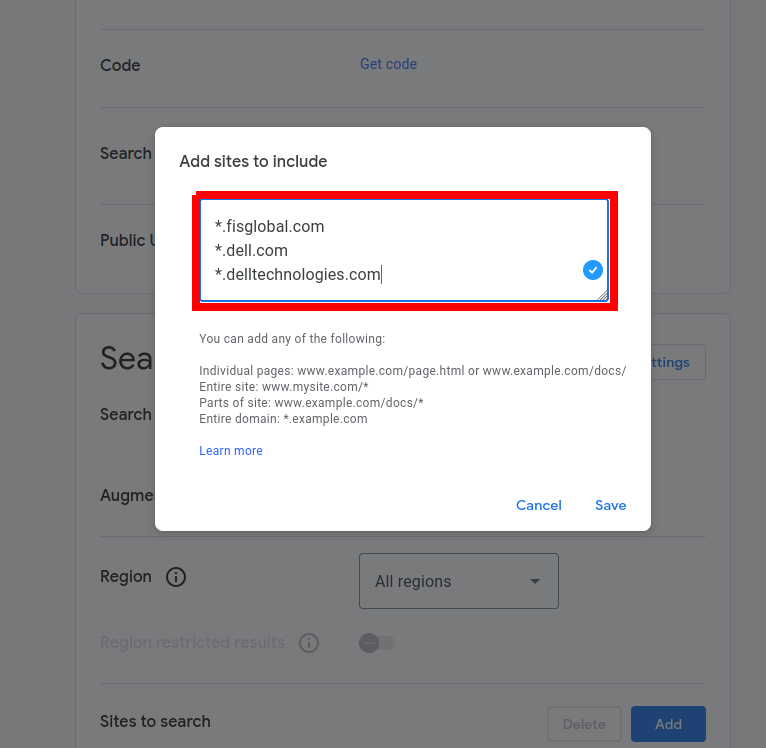
To copy all bug bounty programs with rewards, you could use this CLI one-liner script in your terminal (just make sure you have jq and xclip installed):
curl -s 'https://raw.githubusercontent.com/projectdiscovery/public-bugbounty-programs/main/chaos-bugbounty-list.json' | jq '.programs[] | select(.bounty==true) | .domains[]' -r | sed 's/^/\*\./g' | xclip -selection copyPlace those copied wildcards into the input field and wait till it fully uploads everything. Usually it takes a long time to upload (5-30 minutes), so don’t think that it’s crashed. Once fully loaded, click on Public URL and try searching some sensitive stuff:

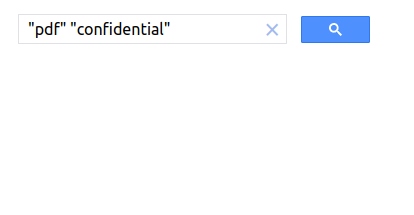
Note that you will get results, only from provided domains! I suggest you to go now to the Google Dorking Database to get some ideas what can be done with this powerful search engine.
Before you go…
As you can see, even if traditional Dorking is less effective nowadays, there are still some methods to achieve the same goal. This article explored three unconventional techniques for mass Google Dorking, shedding light on lesser-known strategies.
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
