Find Sensitive Files with FFUF
The majority do not know what could be done after getting pages like IIS, default Apache, or any other webpage without any content. Well, those are fascinating areas to look for hidden treasures. Sometimes you can access truly sensitive files through these pages if you are dedicated enough! It’s time to explore the topic of content discovery.
Choosing Tool For Content Discovery
Firstly, there are a couple of tools that you could use to discover hidden directories and files. My personal favorite is ffuf. I’m using it like 90% of the time. Although for simple runs, dirsearch is a good option. If I aim for recursive content discovery – the feroxbuster looks like a solid option as well. To show all the features of these tools it could take a long time, so I will only show you my favorite tool – ffuf.
Choosing Wordlist For Fuzzing
To discover hidden areas of the website, you going to need to have a good collection of wordlists. If you have seen my Active DNS Recon video, I have mentioned one of the wordlists that I use – Seclists.
Many testers still favor it, even though some of the wordlists might be old, but they update the repository even up to this day. For content discovery specifically, you need to navigate to Discovery -> Web-Content. It really depends on what you are targeting and what you are trying to achieve – which wordlist to choose from. For instance, I like using raft directories wordlists to discover directories initially. Depends on really how many requests the server can handle, according to that I will choose the size of the wordlist on the go. Generally, I recommend starting small and later checking with bigger wordlists.
The next interesting set of wordlists is from Godfatherorwa. It’s pretty good for initial fuzzing if you know or presume which tech stack the server is using.
Even though most of the wordlists were updated 2 years ago, I still get some good hits.
Another one to use if you do not know what are you going after, or you just want to check for general leaky stuff is OneListForAll.
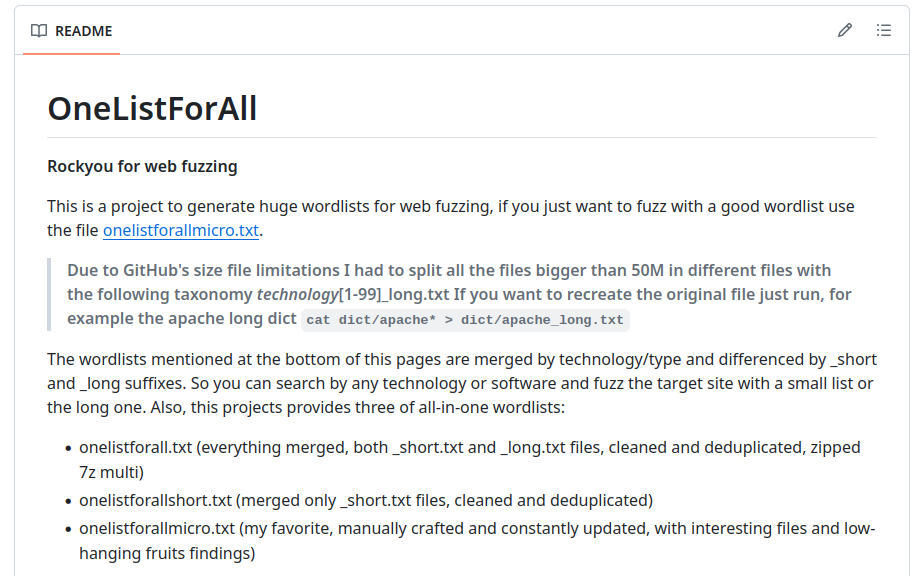
They maintain it pretty well, and if you use its main one, it offers an extremely huge wordlist. As the repository states, it’s rockyou for web fuzzing and if you know what rockyou is, it’s a very huge wordlist with a list of passwords that pentesters use for cracking. Personally, I do use onelistforallmicro.txt initially, then onelistforallshort.txt if I get more interested in that specific target. I only leave the main wordlist overnight in the background when I am going to sleep. If you want to form the main wordlist use olfa.sh file to do so.
The last wordlist is also my favorite when I do not really know what tech stack I am going after initially or sometimes it could be custom fuzzing for certain files.
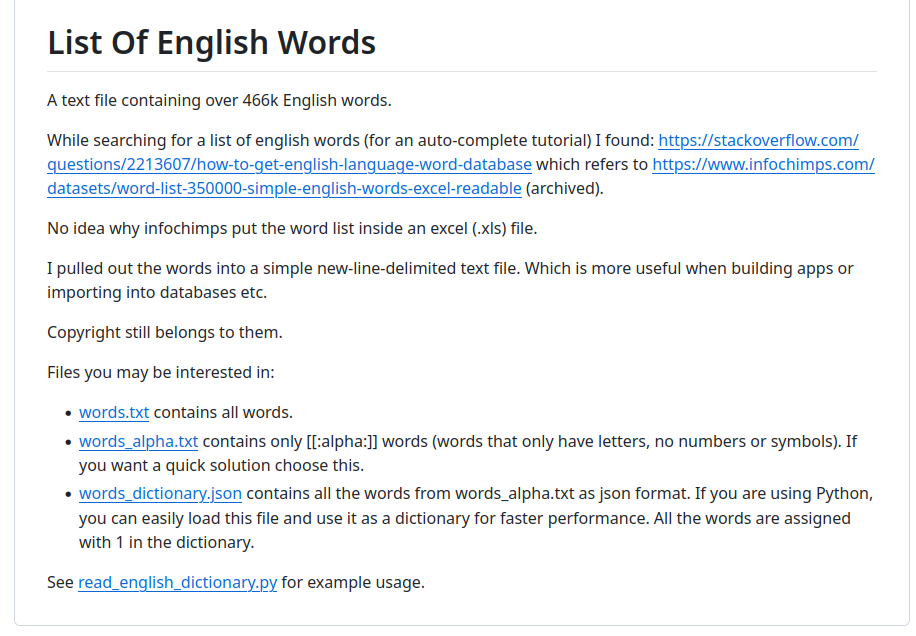
The words.txt file contains an English alphabet almost half a million words. Sometimes I use words_alpha.txt file if I know that there is no case sensitivity on the target server (usually if it’s an IIS server or tech stack that won’t use case sensitivity).
FFUF Main Use Cases
To demonstrate this tool, I will use ffuf.me and labs.hackxpert.com. Firstly, let’s check ffuf.me since it’s a pretty good resource to gain foundational knowledge.
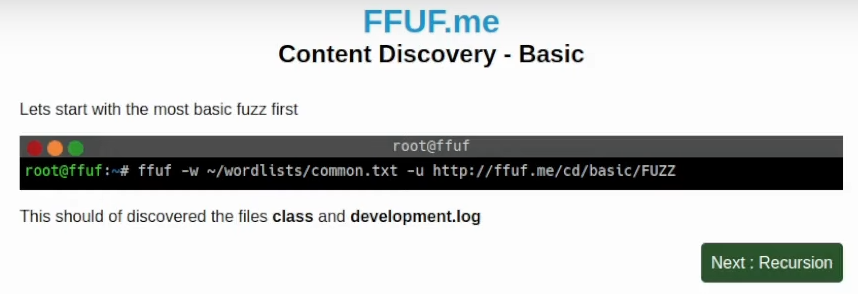
In the first example, this command uses a common.txt wordlist which could be found on the Seclists. It’s also could be used as the first wordlist when you approach your target website. But for me at least, it’s a bit small, since in real-world applications it could be not enough. Usually, I suggest using raft directories wordlist and onelistforallmicro.txt. As an example, I will try onelistforallmicro.txt in the terminal:
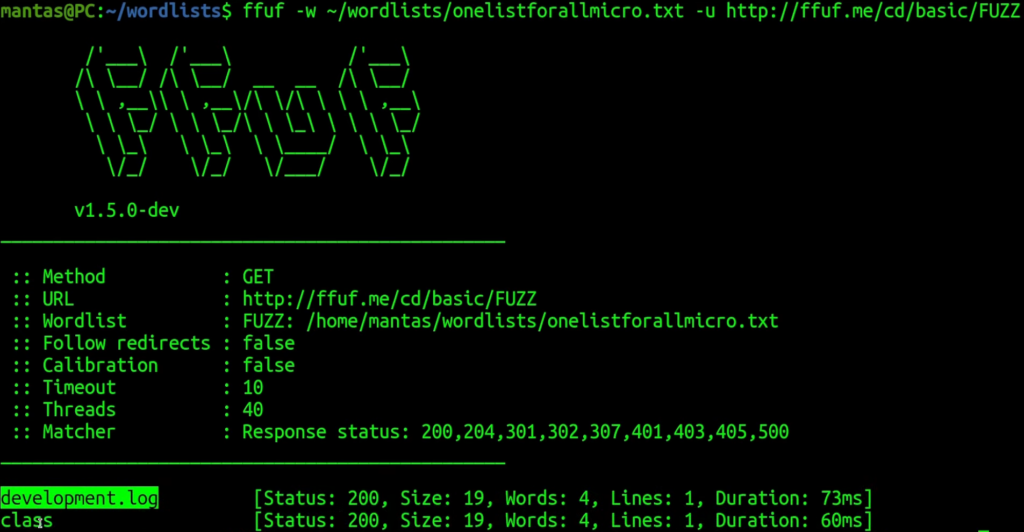
As you can probably see, it was just good enough for this purpose. Now let’s try the next lab:
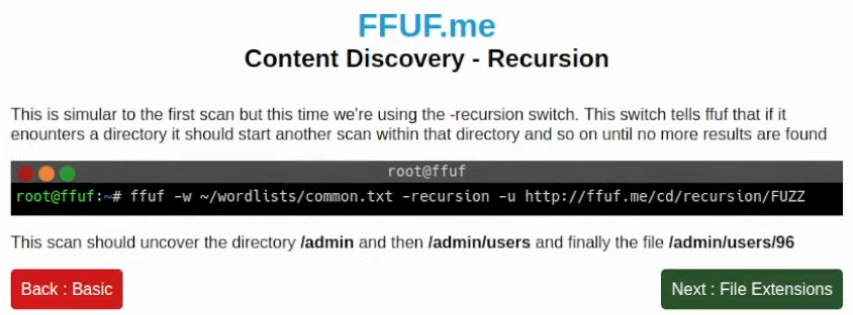
This time, it suggests using a -recursion flag. Usually, for this, I do use a small wordlist with the Feroxbuster tool, but let’s try doing it with FFUF instead. I presume that the mentioned raft wordlist will work just fine in this case:
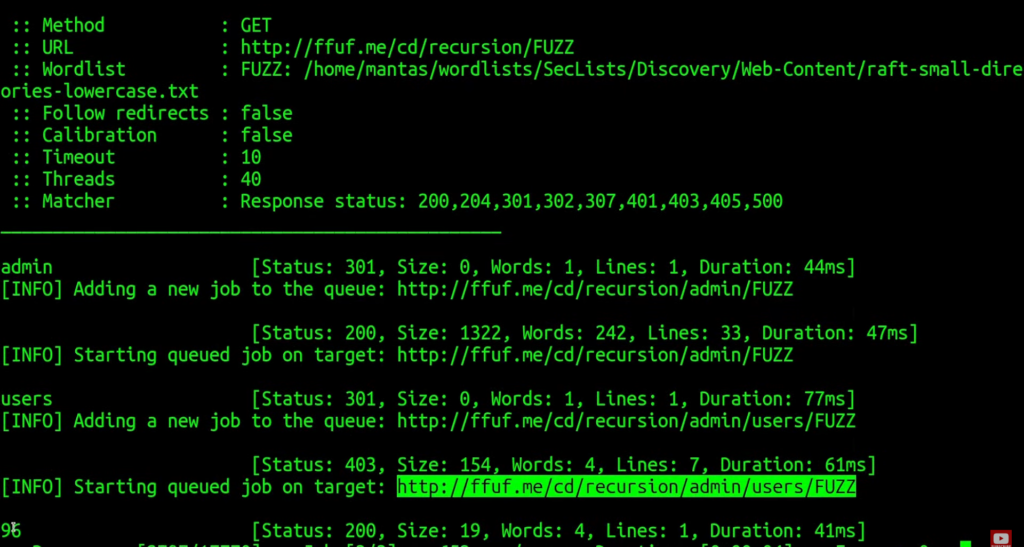
It did succeed in finding a /admin/users/96 endpoint. Let’s try the next lab:
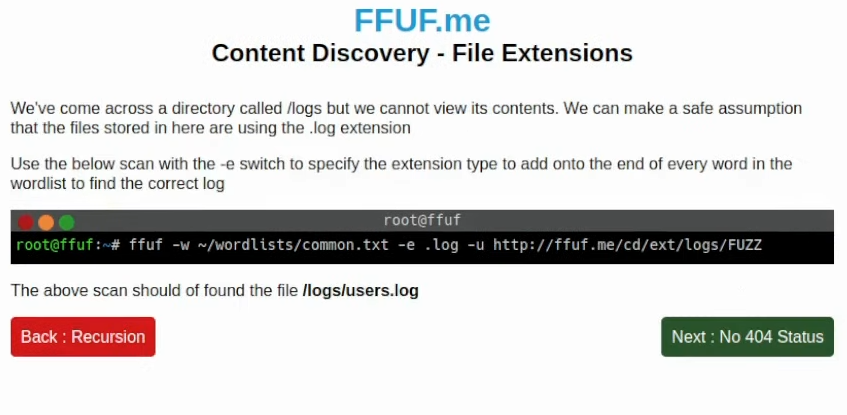
This time it’s about checking file extensions. The ffuf tool has -e flag where you can specify multiple extensions. If you decide to use this one, my recommendation is to use directory wordlists or an English word dictionary if you are going for the long run. Instead of a raft, we can also try using a directory wordlist within the same Seclists directory:
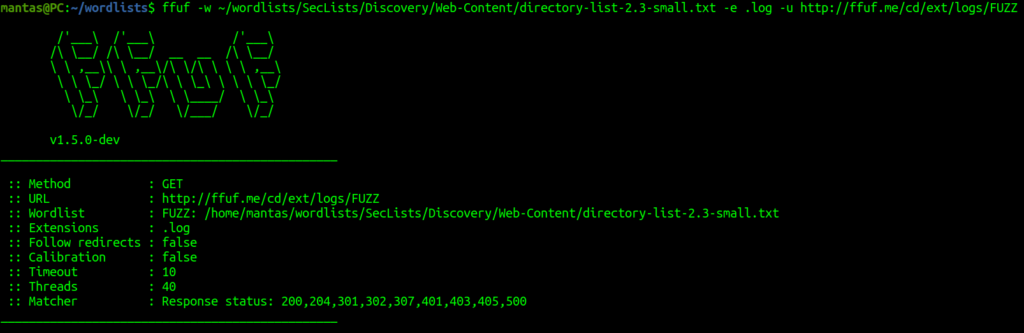
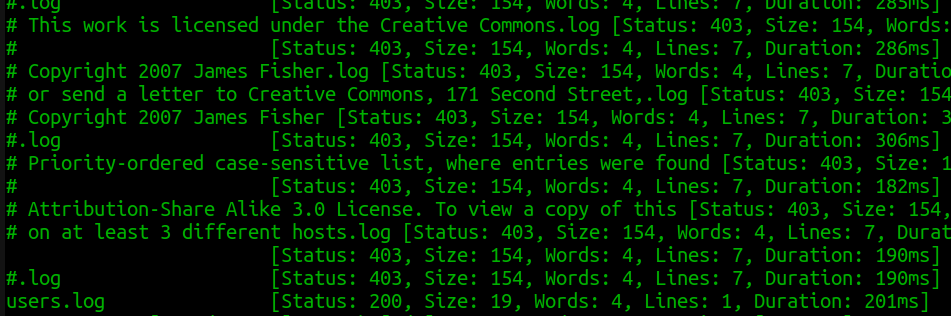
It does indeed succeed. Now in the next lab, we can learn a little bit about filtering:
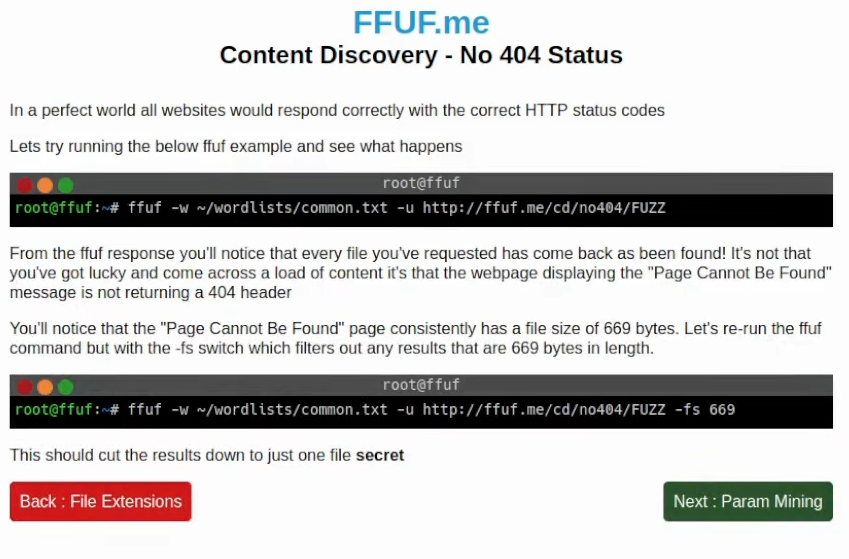
In this example, it shows filtering by response size. The ffuf tool has other filtering options like by words of the response, status code, etc. Time to try with response byte size:
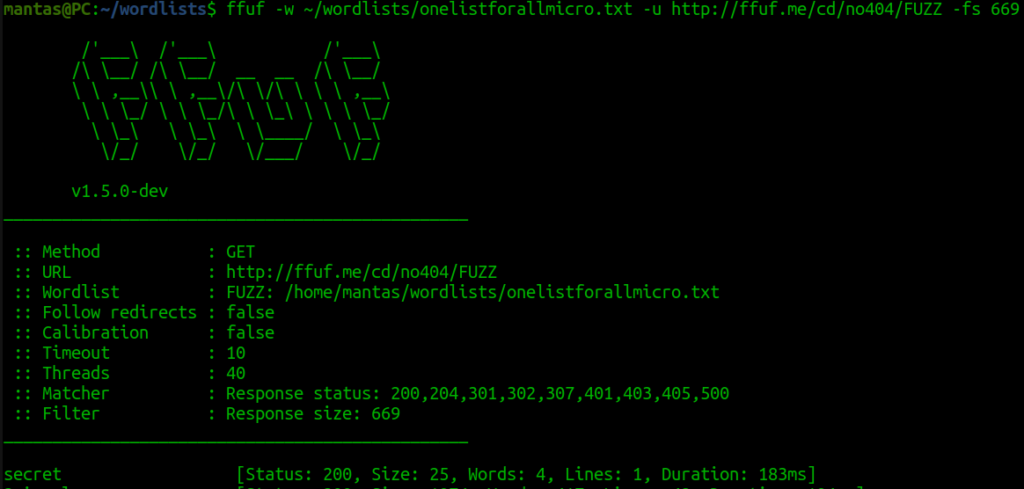
It has succeeded as well. Usually, I use flags like this on the go to filter out a lot of results. Let’s try labs.hackxpert.com right now:
We will explore labs that are actually made for learning about Burps Intruder located at Other -> Fuzzing -> Intruder on the same website.
Let’s try the first lab which is made password guessing from the password list. I will use this list as the wordlist by copying it:
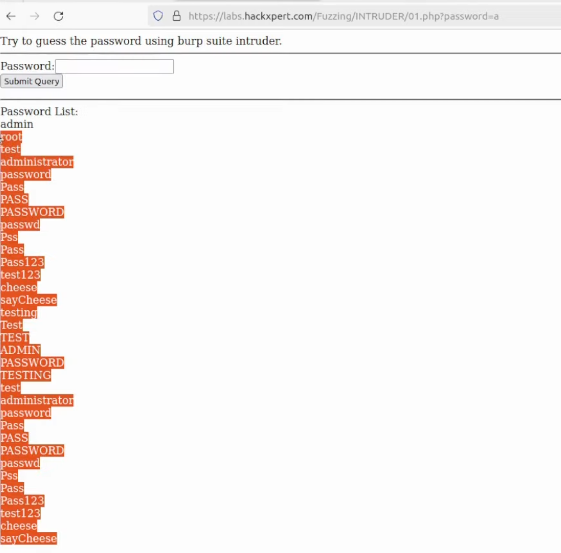
I will just call wordlist “a” and paste my selection:
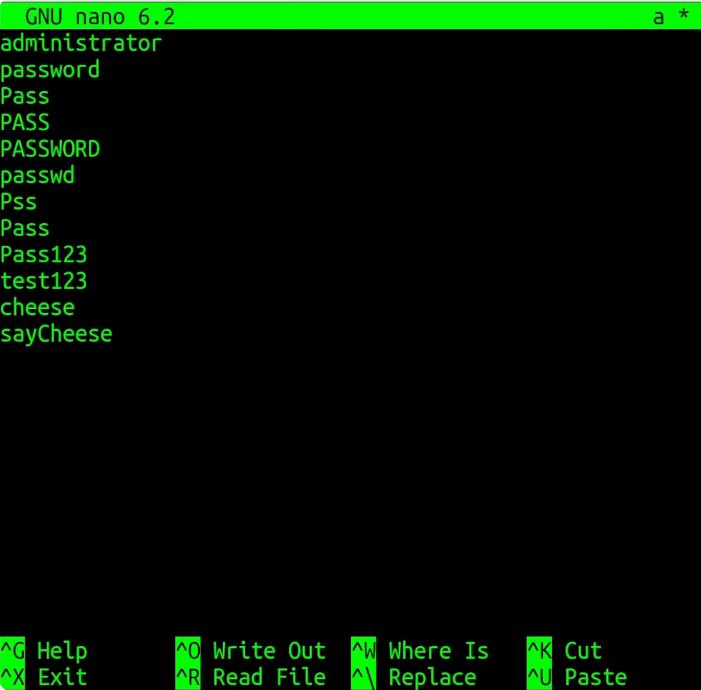
Now it’s time to use ffuf. I’ll use -u flag and pass “a” as the wordlist. I’ll use “FUZZ” and for the wordlists:
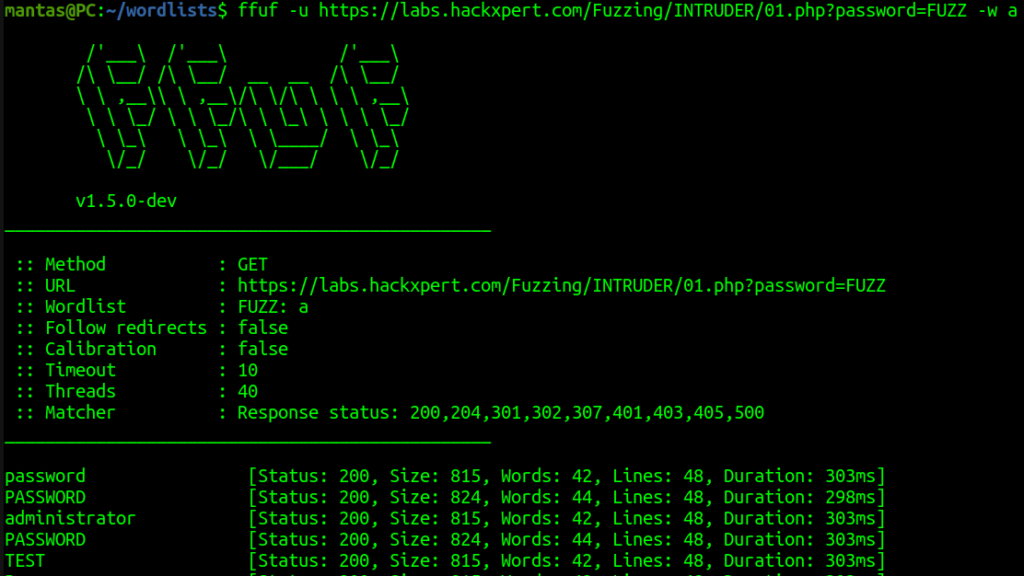
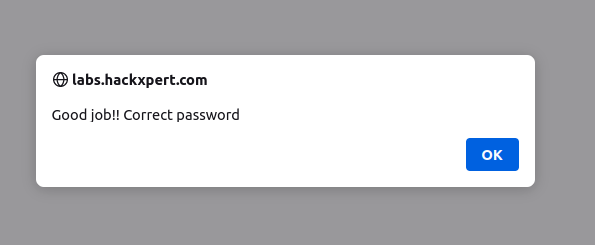
I was not using -fs flag this time, as the wordlist only contains 34 lines, I could inspect each line pretty fast. Usually, you want to use -fs for filtering out responses by size, -fw – by words, and/or -fc – by status code. From the screenshot above we can see that the string “PASSWORD” has a different response size. Let’s try submitting the query here and as you can see – it’s the correct password:
Let’s try the second lab. You will need to guess the correct number between 0 and 100:
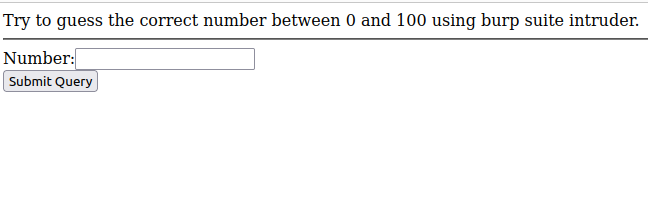
In this case, you need to be a little bit more tricky – not use default wordlists. You could alternatively create yourself. I will use bash for this. You can use any other programming language or you can even generate it online but I will try using my bash skills:
rm a && for i in {1..100}; do echo $i >> a; doneNext, run our fuzzer with the following command:
ffuf -u https://labs.hackxpert.com/Fuzzing/INTRUDER/02.php?password=FUZZ -w a -fs 432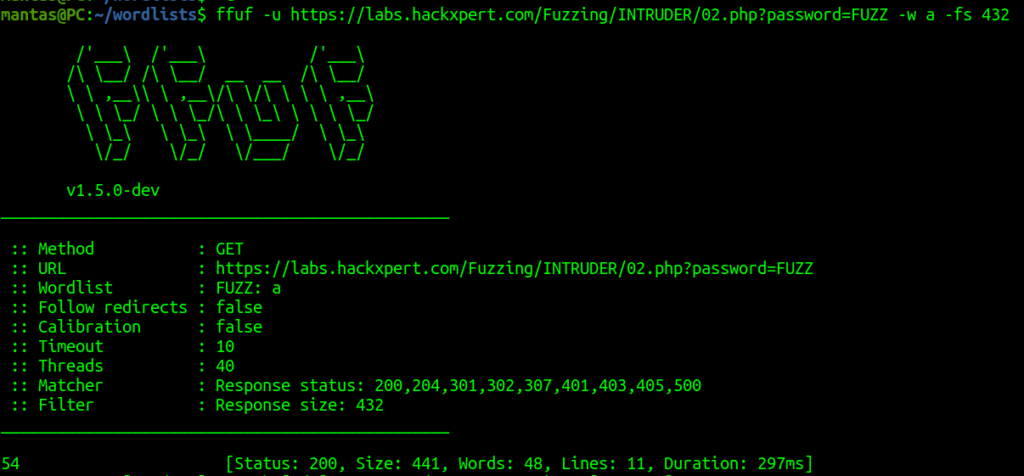
This time I used the filter by the response size of 432 and the value of 54 number was correct.
Last Thoughts
Use this knowledge that we learned today, just for Content Discovery. These were just the initial steps for learning content discovery.
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
