DNS Bruteforce using AXIOM
Are you interested in getting a lot of subdomains of big targets? Using tools like amass or subfinder is not enough for subdomain discovery. Let me guide you through how you can do active DNS Recon using puredns. There is a big difference between how you can collect subdomains. The vast majority of people are just using tools like amass or subfinder which both are pretty good for passive DNS Recon but you will need to do active DNS Recon as well. To put it in simple words, the active DNS Recon is just guessing subdomains. I want to emphasize that this is only useful for big targets that should have a lot of subdomains. Think of companies like Apple, Google, Microsoft, etc.
Choosing Wordlist For DNS Bruteforce
To start, the first thing is to have a good wordlist, or wordlist generated according to your target subdomain keywords. You will want to use that wordlist along with the puredns tool, but firstly let me show you the wordlist that you could use to start.
dnscan wordlist
The first one is it’s the repository of dnscan tool but this repository along with the tool itself, has various subdomain lists. It’s good when you are testing just very quickly. It has a list of the most common subdomain words of 10,000:
Seclists
The next one is seclists but it’s like an OG wordlist for a lot of things like fuzzing, discovery, DNS bruteforce and other interesting stuff for cybersecurity. It’s like oldest repository for security-related stuff, so it’s still good nowadays but you should go to discovery->DNS and there are like couple of wordlists still useful to this day:
If you want the largest dataset, you should go for dns-jhadix.txt. This one I think it’s like the top that has most of the words but there are a couple of others.
Assetnote’s wordlist
The last one which has the most words is from the wordlists.assetnote.io website. The biggest DNS wordlist has over 2 million words! It’s dataset generated by bigquery. You can download it, just click here and you will download a lot of words that could be useful for subdomain enumeration:
Preparing The Big Scans
For this demonstration, I will use the assetnote’s subdomain wordlist. I will spin the AXIOM fleet of 20:
axiom-fleet -i 20After spinning the 20 instances, the next thing that you want to do is create a file containing the same amount of lines as there are your AXIOM instances. In my case, it’s 20, so I will use for loop:
for i in {1..20}: do echo "apple.com" >> target.txt; done
For every AXIOM instance, I will use apple.com with the different sets of wordlists. In this case, I have a couple of modules for AXIOM but the first module that I want to use is just to update the resolvers:
[{
"command":"curl -silent https://raw.githubusercontent.com/trickest/resolvers/main/resolvers.txt > /home/op/lists/resolvers.txt",
"ext":"txt"
}]Let’s pass target.txt to update-resolvers AXIOM module (~/.axiom/modules/update-resolvers.json):
axiom-scan target.txt -m update-resolversAfter updating resolvers, I want to split the DNS worldlist that I will be using. In this case, it’s assetnote’s wordlist with 2 million subdomain words, and surprise surprise I have also another AXIOM module for that (~/.axiom/modules/split-wordlist.json):
[{
"command":"mv input /home/op/lists/wa.txt",
"ext":"txt"
}]It’s basically just from the input that I will provide will split it evenly across all AXIOM machines. The output will be saved to the /home/op/list/wa.txt file in each machine. To run it, I will use another AXIOM scan, pass that assetnote’s wordlist of two million subdomains, and use the module called split-wordlist:
axiom-scan 2m-subdomains.txt -m split-wordlistFinally, I want to use puredns and for that, I have another AXIOM module as well (~/.axiom/modules/puredns-bruteforce.json):
[{
"command":"/home/op/go/bin/puredns bruteforce /home/op/lists/wa.txt --domains input -r /home/op/lists/resolvers.txt -q -w output",
"ext":"txt"
}]It will use puredns with the bruteforce module, splitted part of assetnotes wordlist, for domains it will use apple.com, your updated resolvers list and it will merge the output after the scan is done. Let’s try running it AXIOM scan:
axiom-scan targets.txt -m puredns-bruteforce -anew apple.txt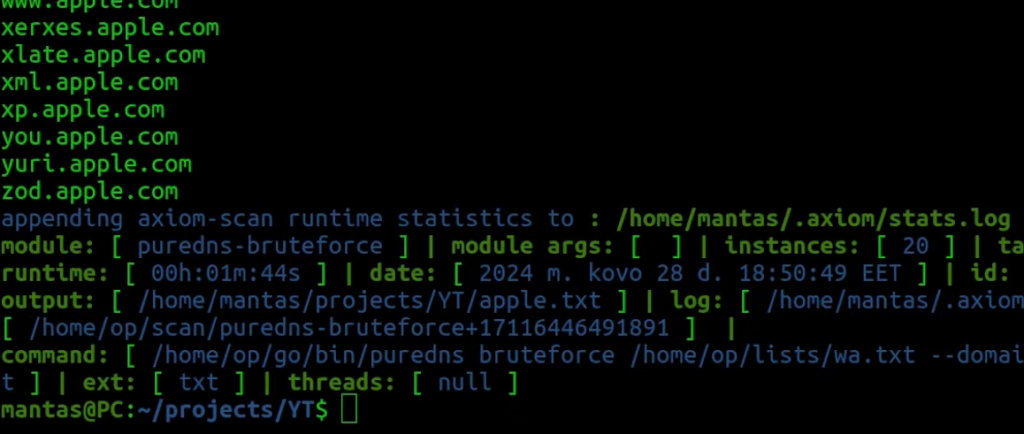
For me, it took less than 2 minutes and it almost had 600 results. Of course, it’s not a lot but if you try a different wordlist or generate specific to your target, those results will add on. Ideally, you want to merge amass, subfinder, and DNS bruteforce recon data.
Final Stuff
If you find this information useful, please share this article on your social media, I will greatly appreciate it! I am active on Twitter, check out some content I post there daily! If you are interested in video content, check my YouTube. Also, if you want to reach me personally, you can visit my Discord server. Cheers!
